DDoS
Distributed denial-of-service (DDoS) DDoS attacks refer to a malicious actor or actors temporarily or indefinitely disrupting services of a host connected to a network to render an entire network or website unavailable.
Volumetric attacks use techniques to attempt to overwhelm the available bandwidth at the target to amplify the amount of traffic received by the target.
Protocol attacks are those that specifically target the ability of network infrastructure to track and handle traffic. Examples include TCP Syn and TCP Ack flooding.
Application attacks are those that target higher level protocols, the most frequently observed being HTTP GET floods, TLS renegotiation, and DNS queries.
Multiple Vector as the term “multiple-vector” these are forms of attacks which leverage more than one of the above methods.
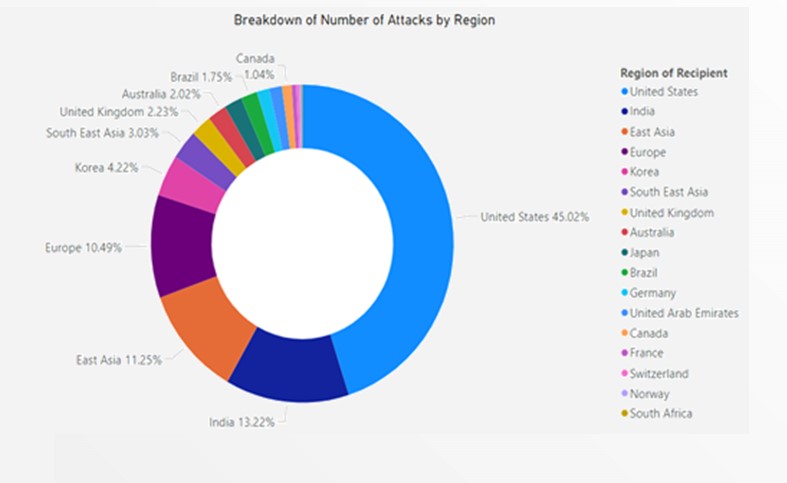
The rising adoption of smartphones and popularity of online gaming in Asia will likely contribute to increased exposure to DDoS attacks. This also applies to countries accelerating digital transformation and cloud adoption.
DDos myth
Since data is not stolen these data are okay: Granted that DDoS attacks do not directly attempt to steal data. But the impact on businesses from the perspective of reputation, credibility, website performance etc. is enough to impact revenues negatively.
They just target websites: These attacks do primarily target websites, but any device that is connected to the internet is vulnerable for an attack or impact. The infrastructure of a company and its resources are prone to being affected as well.
Their impact is not big enough to worry about: A DDoS attack can cost a company millions which is not a small amount. Also, imagine if an ecommerce site is taken down for a couple of hours during a major season sale/offer period. Imagine if your business gets disrupted for couple of hrs.
Nepal DDoS Summary
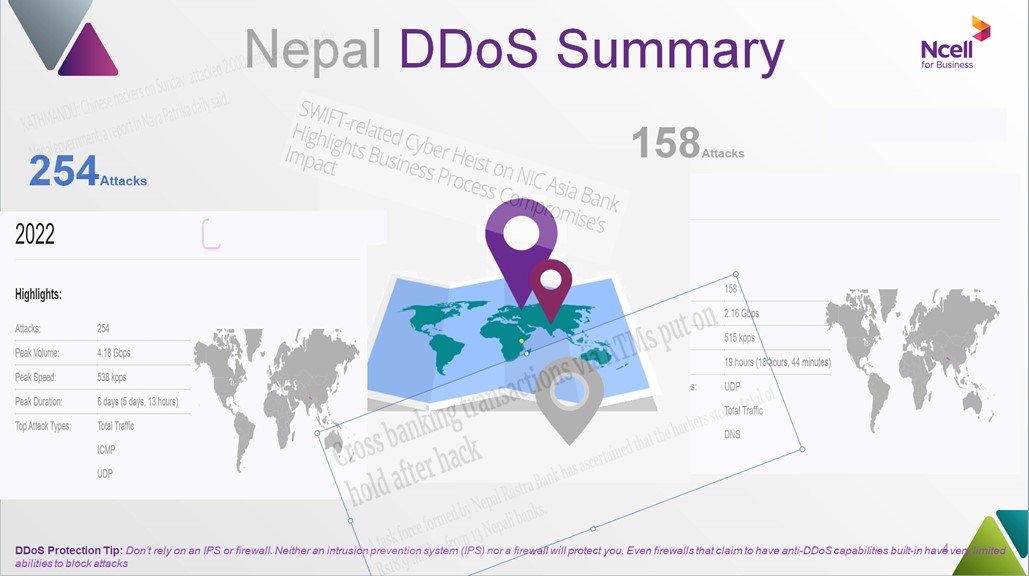
What can we expect?
We can expect to see a continuing trend of increases in DDoS events and the peak bandwidth they will exhibit.
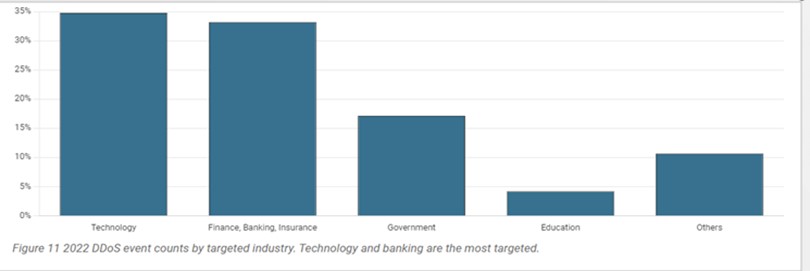
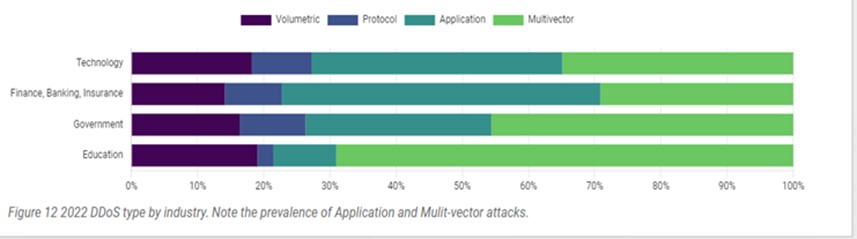
Application vectors are becoming more and more common, with the second most common combination being Multi-vector approaches. All industries should expect these trends, but larger companies whose business relies on the availability of web applications should pay special attention to web-based denial of service.
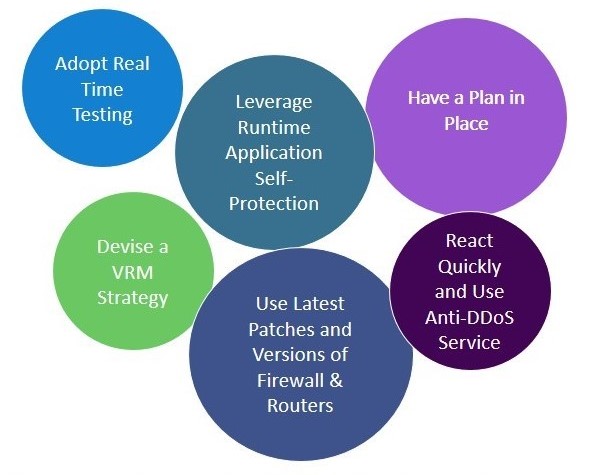
Preventing DDoS Attack
Ncell Recommended Offer
Silver (Rs. 60/Mbps)
• Mitigation of capacity to specific Unit
• Post exceed perform destination blackholing
• Monthly Reports
Platinum (Rs. Post Discussion/Mbps)
• Mitigation of capacity will be 3x the total capacity and unlimited incident handling.
• Clean traffic for any number and duration of incident.
• Monthly Reports run through with technical Expert
• Dedicated UI Interface
Gold (Rs. 80/Mbps)
• Mitigation of capacity to specific Unit
• Post exceed perform 24hrs Mitigation and then destination blackholing
• Monthly Reports
• Dedicated UI Interface
Email us: corporatesales@ncell.axiata.com










